← All Tutorials
Data encryption in backup operations. How to protect your privacy
Data encryption is a critical aspect of backup operations and one of the key elements that backup software must consider. Not only has it become a necessary measure to ensure security, but it is also required to comply with current regulations.
Every day, thanks to the use of mobile devices and various IT applications, we generate and manage a significant amount of data.
In particular, when dealing with sensitive and personal data, it is crucial to ensure their protection.
Encrypting disks and files helps protect data from theft, loss, or improper disposal of physical devices.
Why is it important to encrypt backup data?
As you can easily imagine, making a complete copy of all the data on a computer and storing it in one location represents a significant risk. In the event of theft or accidental loss, the security of the company or individual could be seriously compromised. A prime example is health data, which could cause enormous damage if it falls into the wrong hands.
The GDPR, which came into force in May 2018, also emphasizes data encryption.
Specifically, Article 32 outlines guidelines for ensuring Data Processing Security.
In addition to encryption techniques, it is essential to also provide strong awareness training so that adequate behavioral measures are adopted at all levels, such as securely managing encryption passwords.
How secure are network backups?
We know that storage devices, such as hard drives, are prone to wear and damage.
Therefore, it is essential to perform regular backups of data to store in a secure environment, ideally separate from where the main copy is stored.
In this context, cloud backups or NAS can be an ideal solution.
When data is stored on remote servers, it is crucial to protect the information with an encrypted backup.
There are two main encryption methods for online backups: one server-side and the other client-side.
In the first case, encryption occurs on the host server, while in the second case, it happens directly on the client before the data is sent to the target server.
Often, when discussing online backups, there are concerns about the security of data during transfer or if they are stored on remote servers.
Iperius Backup addresses these concerns by offering client-side encryption, ensuring that data is properly encrypted before being uploaded to cloud services.
Encryption Algorithms
Encryption is the field that studies and develops methods for encrypting and decrypting data.
The process relies on functions that take plaintext input and turn it into encrypted output through substitutions or encodings.
To complete the encryption process, a decryption algorithm is also required, which performs the inverse operation.
There are two main types of algorithms:
- Symmetric key
- Asymmetric key
In the first case, there is a single key used for both encryption and decryption.
In the second case, encryption and decryption keys are separate and use pairs of public-private keys.
In this model, both the sender and recipient have a public key (distributed to everyone) and a private key, which remains secret.
This system was introduced to avoid the need to communicate the decryption key to the recipient, as is done in symmetric key encryption systems. One key is used for encryption, and the other for decryption.
The asymmetric key is used, for example, in digital signatures, where the message is signed with the sender’s private key, and anyone with the sender’s public key can verify its authenticity.
The most widely used algorithm for encrypting data, including backup data, is symmetric key encryption. Some common algorithms include:
- DES – Data Encryption Standard (56 bit)
- 3DES (a key that is three times the length of DES)
- AES – Advanced Encryption Standard, which supports 128, 192, and 256-bit keys.
In particular, AES is the standard used by the U.S. government to protect classified information: 128-bit keys are classified as “secret”, while 192 and 256-bit keys are considered “top secret”.
Iperius Backup uses the AES-256 algorithm for encrypting backups.
Note that algorithms such as DES and 3DES have become outdated and vulnerable due to technological advancements.
How to encrypt data with Iperius Backup
Here are the steps to encrypt your data to create a secure backup.
First, let’s create a new backup operation.
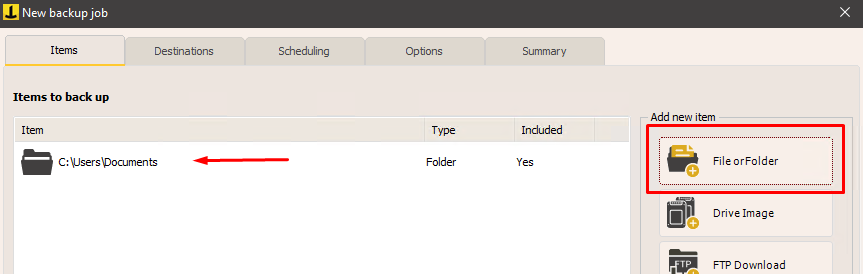
Choose the source folder, for example, select a local folder:
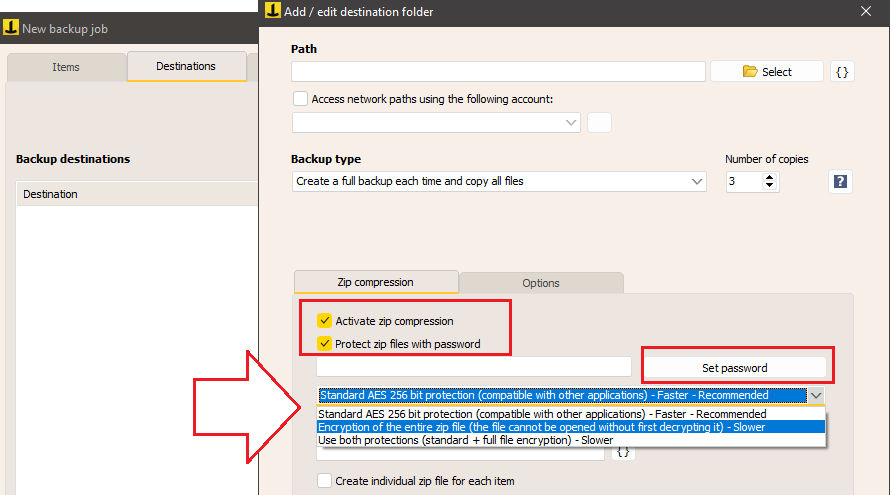
For the backup destination, we can choose from:
-
- a local folder;
- a tape drive;
To enable encryption, after selecting the destination, activate the options “Enable zip compression” and “Protect .zip files with password”, then choose the type of encryption between Standard Protection, Encryption, or both.
Finally, set the password.
At this point, you can add additional details, and your backup is ready to be encrypted.
This tutorial focuses on backup data encryption, but Iperius Backup offers many more features.
Discover all its options by visiting the dedicated page.
For any questions or doubts regarding this tutorial,
Contact us